IT Risk Assessment Template
Stay secure and prepared by improving your risk visibility with Wrike’s IT risk assessment template. Better manage and mitigate the risks that impact your organization.
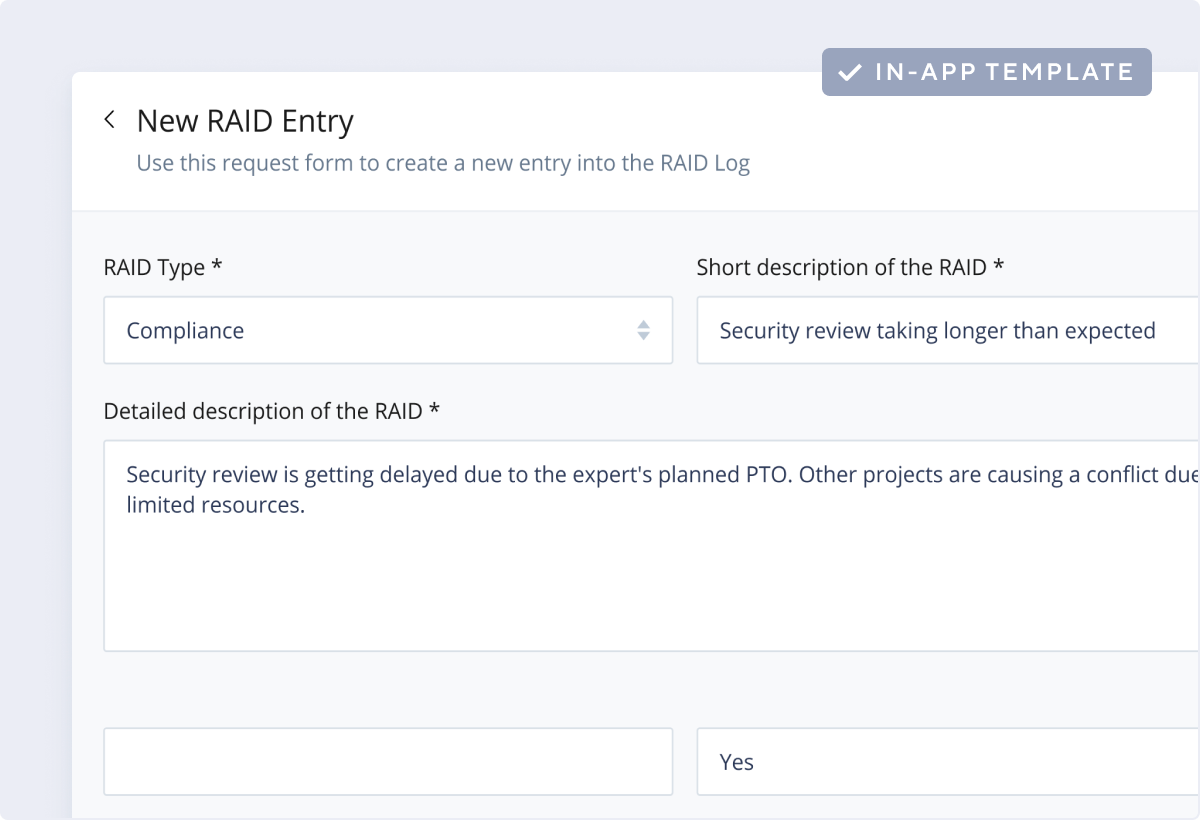
Wrike’s IT risk assessment template helps your team better manage risk and resources. This template enables you to easily create and submit new RAID logs, visualize risks across multiple teams and projects, and distribute resources more efficiently.
Any team that regularly encounters risks can use this template effectively. The IT risk assessment template simplifies the reporting process for anyone experiencing risk, while providing risk managers with better visibility and detail into each report.
Enter your business email linked to your Wrike account to gain instant access to this template.
Yes, the IT risk assessment template is completely free.
You can only access this template when you create a new space. You can access the use case templates gallery through the space creation wizard. When you opt to create a new space, the template gallery opens by default.
Yes, there are.
Check the prerequisites above. If you don’t match one of the prerequisites, talk to your space admin or your account owner. If you match all the prerequisites and you still can’t see the “Risk assessment“ template, feel free to reach out to the Wrike support team.